Hosting web applications on the internet is a risky business. Bad actors have a myriad of tricks to steal, extort, and damage your visitors, data, and reputation. This requires vigilance to reduce and eliminate potential vectors of attack in the entire stack of a website, from the firewall to the web server to the application tier to the client-side markup and scripts. This article will focus on activities to take when your application tier is using the DNN Platform, and will not primarily discuss the other components in a website’s stack (which others have done).
Upgrade
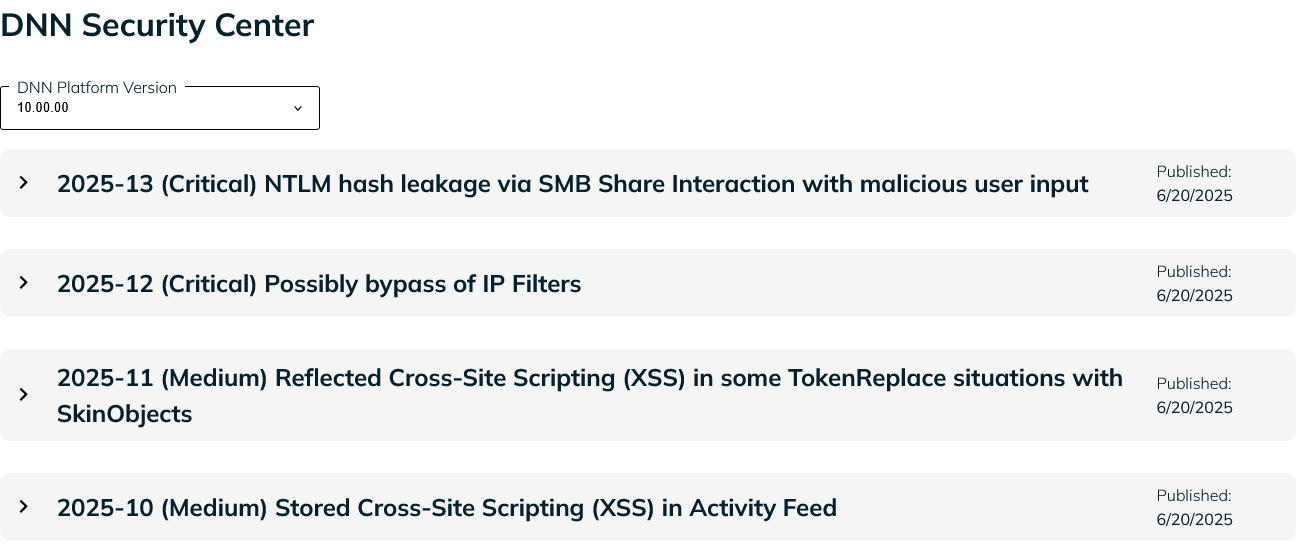
The most important step in keeping a DNN site secure is to regularly upgrade to the latest version of DNN. The Security Center indicates any known vulnerabilities in a particular version of DNN; however, even if there are not any known vulnerabilities right now, it’s still advisable to keep up with upgrades. In addition to non-security bug fixes, getting in the habit of upgrading makes it simple to get secure before a vulnerability is disclosed, rather than having upgrade issues when it really matters.
Telerik
In 2009, DNN 5.2 introduced the Telerik ASP.NET RAD Controls component suite through a special license agreement. That license agreement ended in 2013, and every version of DNN since that point has included the 2013 version of the component suite. A variety of security issues in the component suite were identified over the years, with a patched version released in 2017. However, even with the patch, there are still known vulnerabilities that result from having the Telerik dependency (even if it’s not actively used). In 2020, DNN 9.8.0 was the first version which completely supported removing Telerik without reducing functionality (through replacing the Asset Manager), and in 2022, DNN 9.11.0 stopped distributing the Telerik components for new installations and enabled automated removal upon upgrades. Now, in 2025, DNN 10 requires removing the vulnerable Telerik components upon upgrade.
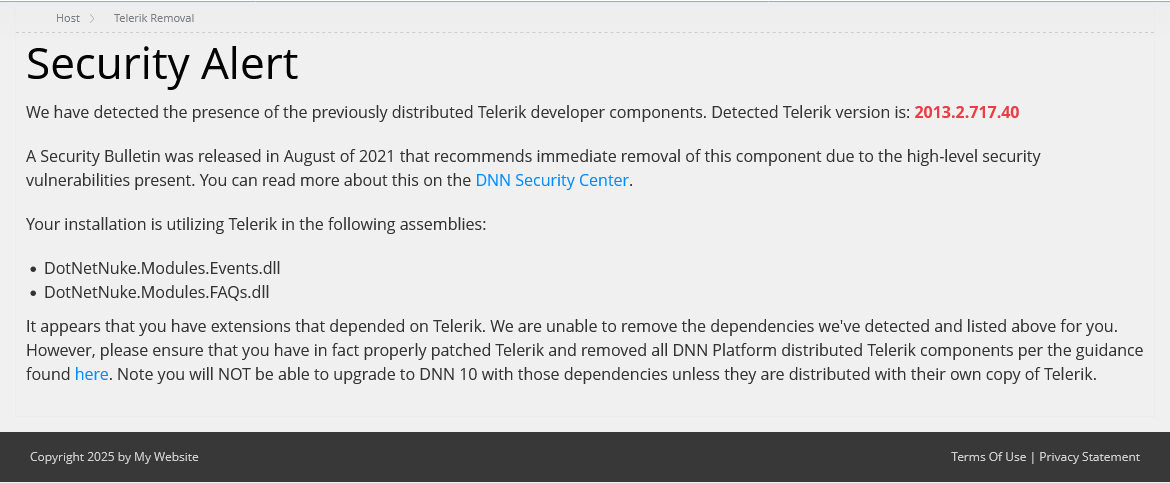
It’s a long story, but the short version is that, if a site is still using the Telerik components, that site is vulnerable to known attacks. The simplest removal strategy is to upgrade to DNN 9.13.9, take a fresh backup of the site, and then go to the Telerik Removal page from the Persona Bar and allow it to automatically remove every component related to the Telerik components. It will provide alerts about 3rd party extensions which have dependencies on Telerik. Those extensions will need to be upgraded, replaced, or removed.
Cloudflare
While working through removing extensions that depend on the vulnerable Telerik components (see above), the best remediation of those vulnerabilities is to use Cloudflare’s CDN and firewall before traffic reaches the DNN site. Cloudflare’s web application firewall (WAF) includes rules which specifically mitigate known vulnerabilities due to Telerik. This is in addition to the standard speed, reliability, and security benefits from introducing Cloudflare’s services (even their free plan includes these major benefits).
Security Audits
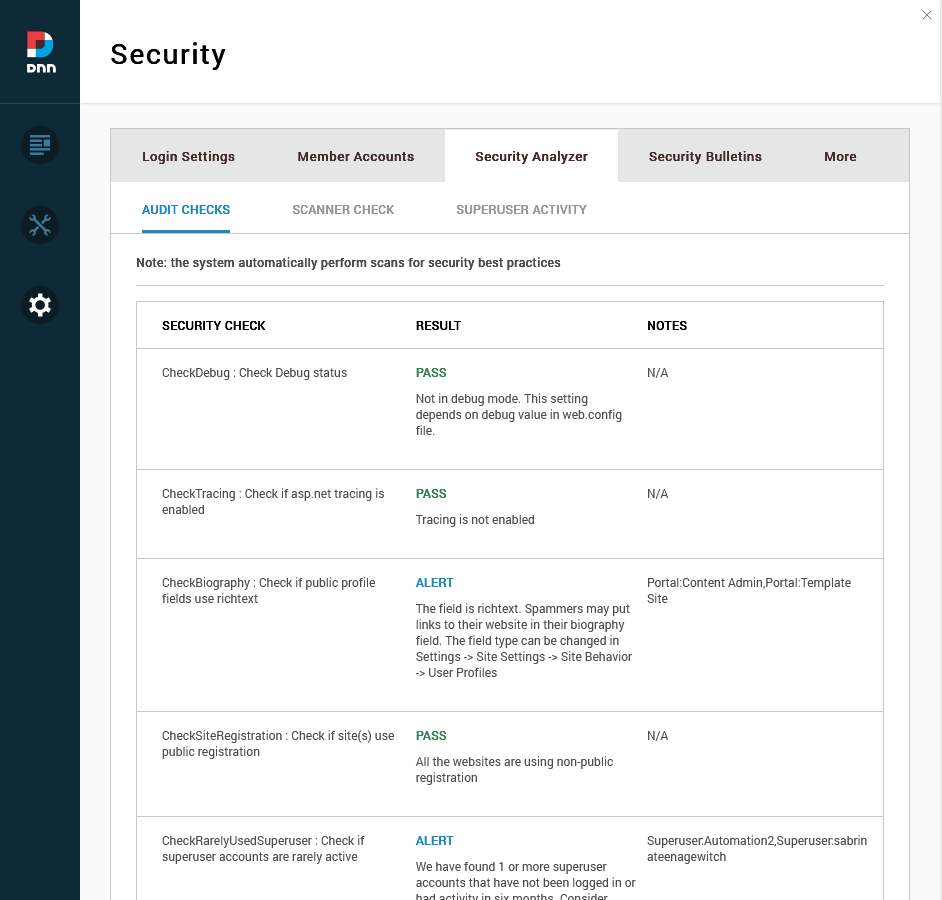
DNN comes out-of-the-box with a variety of security features. As a host/superuser, the Security page of the Persona Bar is available, exposing a number of settings and tools to manage the security of the site. Specifically, the Security Analyzer tab provides a number of checks which can identify well-known misconfigurations to investigate within the site.
Super Users
Super User (also known as Host) accounts have full access within a DNN site, and therefore it is imperative to monitor and reduce access to those accounts as much as possible. The Security Analyzer (mentioned above) provides checks for accounts which have not been used recently, and provides a way to audit the last login and activity of these users. Regularly review and remove access for those who no longer need it.
3rd Party Extensions
While it’s important to ensure there are now known misconfigurations of a DNN Platform site, a primary cause of vulnerabilities is from 3rd party extensions, rather than what comes out-of-the-box. It’s important to keep these extensions upgraded, similarly to DNN Platform itself. Removing extensions which aren’t used will also remove potential security holes they may have introduced, and will reduce the burden of keeping up with upgrades.
Summary
There are many resources available to keep a DNN site secure. Upgrading it regularly will be a big step, while removing outdated extensions closes off another major vector. Review the built-in security audits to go deeper, and add Cloudflare in front of the site to stop attackers before they even get to the site. Security on the internet is a constant tension, but the DNN Platform is a strong, secure foundation for web applications.